MCS022 Solved Question Paper 2017
MCS-022 Previous year solved question paper. Ignou solved question paper 2017. MCS022 solved quetion paper. MCS022 Assignment. Ignou Assignment mcs022.
Term-End Examination December, 2017
MCS-022 : OPERATING SYSTEM CONCEPTS AND NETWORKING MANAGEMENT
1. (a) Define a Real Time Operating System. Give any two examples of a real time operating system. What are the most important issues in the design of a real time operating system ?
Sol : Real-time Operating System
The main characteristics of the real-time systems is the correctness of the computation. Adistinct feature of real-time systems is that jobs have completion deadlines. A job should be completed before its deadline to be of use (in soft real-time system) or to avert a disaster (in hard real-time systems).
A real-time operating system (RTOS) is an operating system with two key features: predictability and determinism. In an RTOS, repeated tasks are performed within a tight time boundary, while in a general-purpose operating system, this is not necessarily so.
RTOSes are subdivided into “soft” real-time and “hard” real- time systems. Soft real-time systems operate within a few hundred milliseconds, at the scale of a human reaction. Hard real-time systems, however, provide responses that are predictable within tens of milliseconds or less.
Examples of RTOS is : process control, air traffic control, guidance of missile systems.
Design Issues : The major issue in the design of real-time operating systems is the scheduling ofjobs in such a way that a maximum number of jobs satis@ their deadlines. Other issues include designing languages and primitives to effectively prepare and execute a job schedule.
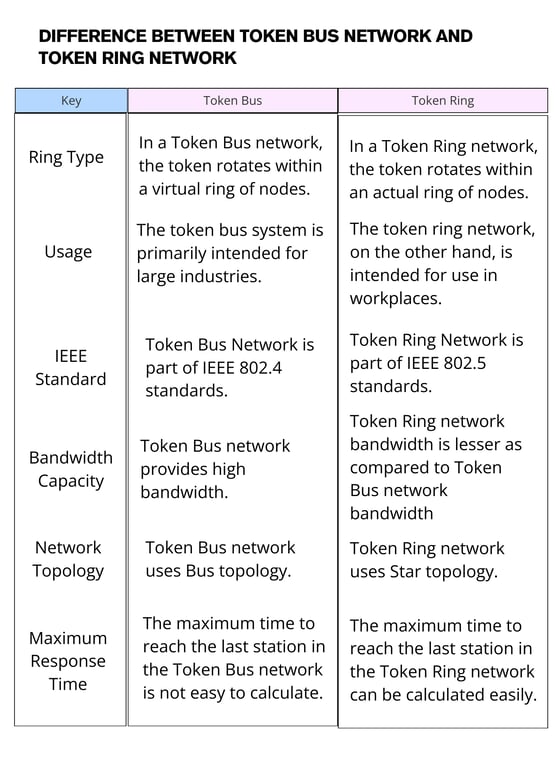
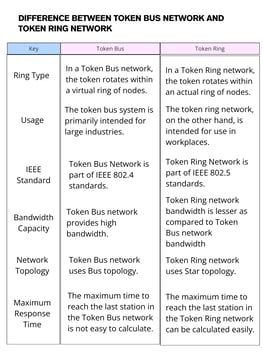
(b) What is Token Ring ? How does it work ? Differentiate between token ring and token bus.
Sol : Token Ring is network used in LAN. And it is used in token passing. In token-passing networks such as Token Ring a special network packet called a token is passed around the network from device to device. When a device has data to send, it must wait until it has the token and then send its data. When the data transmission is complete, the token is released so that other devices may use the network media.
In other words A token ring is a data link for a local area network (LAN) in which all devices are connected in a ring or star topology and pass one or more tokens from host to host.
(c) What is meant by Trust Relationship ? Discuss the role of Kerberos and Domain controller in maintaining trust relationships.
Sol: . A trust relationship is an administrative link between two domains. A domain tliat trusts another domain is called a TRUSTING domain and the other domain is called TRUSTED domain. Tlie TRUSTED domain or Accounts domain holds the user accounts and the TRUSTING domain or RESOURCE domain holds the resources. The trust is only one-way, meaning that if domain A trusts domain B, then domain B does not have to trust domain A. In order to have trust in both directions, two one-way trusts relationsllip needs to be created.
Kerberos: When a user the log on process by entering his credentials, Windows will contact an Active Directory domain controller, and locate the Kerberos Key Distribution Center (KDC). An Authentication Server (AS) performs the actual authentication. The KDC responds by issuing a Ticket Granting Ticket (TGT) to the authenticated user. The TGT contains identification information about this user to various servers on the network, and is used to gain further access in the network. After the user account has been authenticated, the TGT is used to request further Kerberos tickets in order to access network services. The machine that provides the tickets for the network resources to the authenticated client is known as a Ticket Granting Server (TGS).
Domain Controller : Domain controllers are systems that run NT Server and share the centralised directory database that contains user account and security information for a particular domain. When users log on to a particular domain account, the domain controllers authenticate the users username and password, against the infoilnation stored in the directory database.
When you perform NT Server installation, you must designate the role that servers will play ill a dornain..Three choices are available for this role: PDC, BDC, and member server.
The Primary Domain Controller (PDC)
The first Windows NT Server in the domain is configured as a primary domain controller (PDC). The User Manager for Domains utility is used to maintain user and group information for the domain using domain security database on the primary controller.
Backup Domain Controllers (BDC)
BDC (Backup Domain Controllers) are the otlier server after one server has been configured as PDC. BDC stores a copy of the Database on the PDC, which is updated periodically to distribute changes made to the main database on the PDC.
(d) Write the Linux/Unix commands for the following :
(i) Show the users logged in on the network.
(ii) List the files having more than one digit in the name.
(iii) Tell the system to run the process continuously even if the user logs out.
(iv) To allow a user to communicate with another user, logged in by splitting the screen and providing two-way communication.
(v) To kill a process after one hour.
Sol: (i)Show the users logged in on the network.--> who command used
Explanation:
who displays the users currently logged into the system, including remote logins over the network.
It shows:
Username
Terminal (e.g., pts/0)
Login time
Remote host/IP (if the user is connected via SSH or network)
(ii)List the files having more than one digit in the name--> ls | grep -E '[0-9].*[0-9]'
Explanation:
ls lists the files in the current directory.
grep -E uses extended regular expressions.
'[0-9].*[0-9]' ensures:
There's at least two digits in the filename (not necessarily next to each other).
Example:
If your directory contains:
file1.txt
file12.txt
test99.log
a2b3c.txt
123.txt
The output will be:
file12.txt
test99.log
a2b3c.txt
123.txt
(iii)Tell the system to run the process continuously even if the user logs out--> nohup command_name &
Explanation:
nohup (no hang up): Tells the system not to terminate the command when the user logs out.
command_name: Replace this with your actual command or script.
&: Runs the command in the background.
Example:
nohup python myscript.py &
This runs myscript.py in the background, and it will keep running even after you log out.
The output (stdout and stderr) is typically saved in a file called nohup.out
(iv) To allow a user to communicate with another user, logged in by splitting the screen and providing two-way communication. -->talk username
Example:
talk user2
How it works:
This starts a two-way chat session with another logged-in user.
The screen is split: your input appears on one half, and their responses on the other.
The other user must also run talk or accept the request when prompted.
(v) To kill a process after one hour.--> sleep and kill command used together
sleep 1h && kill PID &
Explanation:
sleep 1h: Waits for 1 hour (you can also use 3600 seconds: sleep 3600)
&& kill PID: After sleep finishes, it kills the process with the specified PID (Process ID)
&: Runs the whole command in the background, so it doesn't block your terminal
Example:
If your process has PID 12345:
sleep 1h && kill 12345 &
2. (a) List and explain the file systems supported by Linux operating system. Also, write the security features provided by Linux in each file system.
Sol: Linux supports a variety of file systems, each designed for different purposes such as performance, portability, or reliability. Below is a list of commonly supported file systems along with their security features.
In the textbook mentioned on 2 type of file system 1)ext2 and 2)ext3.
But presently there are
ext2
ext3
ext4
XFS
Btrfs
FAT32
NTFS
ISO9660/UDF
1)EXT2 -Second Extended File System : ext2 is one of the earliest file systems used in Linux. It does not support journaling, but it is still used in small storage devices due to its simplicity.
Security Features :
Inode-based file management. Each file in ext2 is associated with an inode, which stores metadata such as file permissions, ownership, timestamps, and pointers to data blocks.
Fast symbolic links. ext2 supports both hard and symbolic links.
No journaling (for faster write performance). Unlike ext3 and ext4, ext2 does not have a journaling mechanism. This means write operations can be slightly faster.
Access control lists (ACLs) support. ext2 includes ACLs, allowing fine-grained permission management beyond traditional UNIX-style file permissions. This enables administrators to set detailed user and group access rights.
Reserved blocks for system processes. A portion of disk space (typically 5% by default) is reserved for system processes and the root user.
2)EXT3-Third Extended File System : It is a journaling file system. When the system crashes, the possibility of file system corruption is less because of journaling. ournaling helps prevent file system corruption by tracking all changes before they are permanently written to the disk.
Security Features:
Journaling
Htree Indexing for Directories: To improve the performance of operations in directories containing a large number of files, ext3 implements Htree indexing, a method that uses a hashed B-tree structure to index directory entries. This mechanism reduces the time required to find files in large directories, enhancing overall system performance.
Support for Large Files and File Systems: ext3 can support files up to 2TB in size and file systems up to 32TB.
Access Control Lists (ACLs) and Extended Attributes: ext3 supports Access Control Lists (ACLs), which provide a more flexible permission mechanism than the traditional UNIX file permissions. Additionally, extended attributes allow users and applications to associate additional metadata with files and directories beyond the standard file attributes.
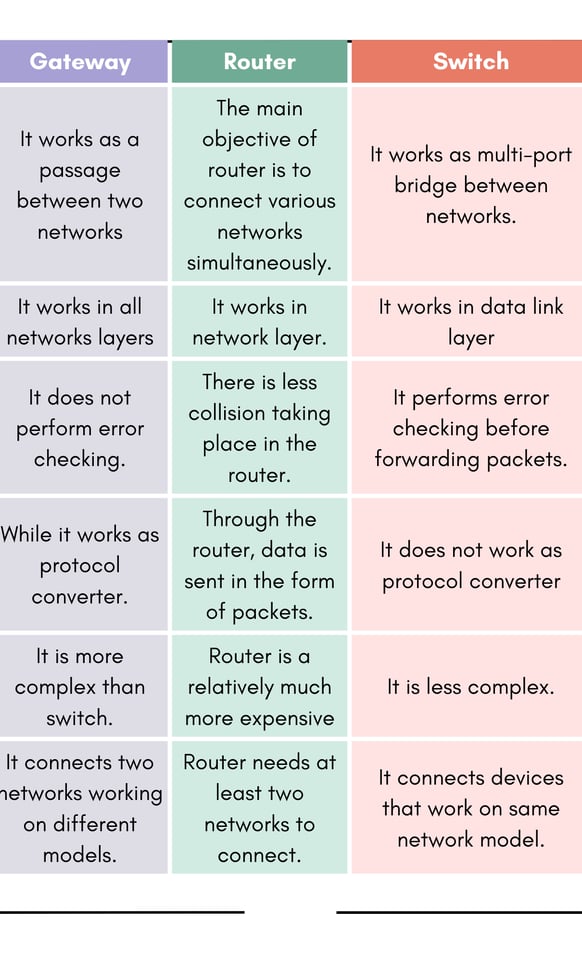
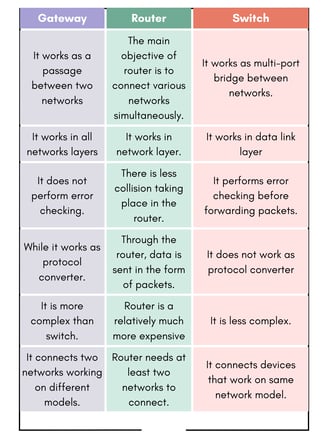
2) (b) Differentiate between gateways, routers and switches.
Sol: Gateways: A Gateway is the Hardware/Software device that is used to interconnect LANs & WANs. Gateways are much more complex and powerful than a router. They are slower than a router and are expensive. A Gateway incorporates the functions of routers and bridges, but it can translate instruction set on sending network into corresponding instruction set of the receiving network. Gateways make communication possible between different architectures and environments.
A Gateway links two systems that do not use the same communication protocols, data formatting structures, languages and architecture, which can not be done by a router.
Routers: A router is a special -purpose computer having a processor (CPU) and memory like any other computer. But unlike any other computer, it has more than one 110 interface that allows it to connect to multiple computer networks. Routers are both hardware and software devices.
Unlike a bridge, a router can connect networks that use different technologies, addressing methods, media types, frame formats, and speeds. Routers are used in complex network situations because they provide better traffic management than bridges. A router keeps track of the address of all the segment of a network and can even determine the best path for sending data. Routers do not pass broadcast traffic. The router examines each packet of data, checks the routing table , and then forwards the packet if necessary.
Switches: A network switch is a networking device that connects multiple devices within a single computer network. A switch is a multi-port bridge with a buffer and a design that can boost its efficiency and performance. It is a data link layer device. The switch can perform error checking before forwarding data which makes it very efficient as it does not forward packets that have errors and forward good packets selectively to the correct port only. In other words, the switch divides the collision domain of hosts.
2. (c) Differentiate between relative and absolute pathnames using an example for each in Linux
Sol: 1. Absolute Pathname
Definition: An absolute pathname starts from the root directory / and provides the complete path to the file or directory, regardless of the current working directory.
Always begins with /.
It is independent of the current location in the file system.
Example: /home/student/documents/file1.txt
This means the file file1.txt is inside the documents folder, which is under student, which is under /home.
2. Relative Pathname
Definition: A relative pathname does not start with /. It specifies the path relative to the current working directory.
It is dependent on where you currently are in the file system.
Example:
If you are currently in /home/student, and you want to access file1.txt inside the documents folder:
documents/file1.txt
This tells Linux to look for file1.txt relative to your current location (/home/student).
Key Differences Table
Feature Absolute Path Relative Path
Starts with / (root) Does not start with /
Based on Root directory Current working directory
Portability Always points to the same location Changes with current directory
Example /etc/passwd ../etc/passwd or documents/
3. (a) Explain the concept of pipes, filters and redirection in Linux operating system. Give an example for each.
Sol: Pipes : The act of connecting the standard output of a command to the standard input of another is also referred to as piping the output of the first command to the second. Pipelines are one of the big strengths of Linux, because they often enable us to group several existing commands quickly to perform a task for which there is no command directly available.
Symbol : |
Purpose:
To connect multiple commands.
To avoid creating temporary files.
Example: [kumarr@,linux kumarr] Is - 1 -p I grep -c ' / $ '
It means that the standard outpu of Is -p is passed to grep.
Filters : A filter is a command which can take its input from the standard input and can produce output on the standard output. You can think of a filter as a "device" placed between the standard input and the standard output which filters the standard input before placing it on the standard output.
Example: cat marks.txt | grep "John"
cat reads the file marks.txt.
grep "John" filters lines that contain the word “John”.
Common Filter Commands:
grep, sort, uniq, cut, wc, awk, sed
Redirection (>, <, >>)
Redirection is used to change the standard input/output of commands.
Symbols:
> : Redirect output (overwrite)
>> : Append output
< : Redirect input from a file
Examples:
Redirect output to a file: ls > filelist.txt
(Saves the output of ls into filelist.txt, This sign indicates that the standard output of the command preceding it should go to the file specified to its right rather than to the terminal screen.)
Append output to a file: echo "Hello" >> filelist.txt
(Adds “Hello” to the end of the file, This sign appends output to the file specified rather than overwriting it.)
Use input from a file: sort < names.txt
(Reads names.txt and sorts the contents)
3. (b) Explain the basic purpose of enabling the offline features in Windows 2000 operating system.
Sol: Offline file allows users to keep copies of network files on a local machine. When say not connected to network, the user can use cached copy. When the user again reconnects to the network, offline file is synchronized with the online copy.
If changes have been made to the offline copy, offline file is copied to the network copy. If network version is changed but offline copy has not changed, the online copy is copied over the users offline versions.
If both online and offline versions of the file have changed, a dialog box appears that lets the user select either of the two versions and also gives an option to retain both the versions of different filenames with the same name.
This feature is useful for:
1. Users working on a network.
2. Mobile Users
3. Users with an unreliable network connection
(c) Write a Linux shell script for automatic grouping of files given in a directory. All files will be grouped on the basis of their size and will be saved into the newly created folders based on file size groups given below : Files will be grouped into 0 to 5 kB, 5 kB to 5 MB, 5 MB to 1 GB and greater than 1 GB. Note : Make suitable assumptions, if necessary.
Sol:
#!/bin/bash
# Step 1: Create folders to store grouped files
mkdir -p group_0_5KB group_5KB_5MB group_5MB_1GB group_above_1GB
# Step 2: Loop through all files in the current directory
for file in *; do
# Step 3: Check if it's a regular file (not a directory)
if [ -f "$file" ]; then
# Step 4: Get the size of the file in bytes
size=$(stat -c%s "$file")
# Step 5: Check file size and move to the correct folder
if [ $size -le 5120 ]; then
mv "$file" group_0_5KB/
elif [ $size -le 5242880 ]; then
mv "$file" group_5KB_5MB/
elif [ $size -le 1073741824 ]; then
mv "$file" group_5MB_1GB/
else
mv "$file" group_above_1GB/
fi
fi
done
# Step 6: Show a completion message
echo "Files have been grouped based on their size."
4. (a) Explain how distributed operating system is better than network operating system.
Sol: The focus of a network operating system (NOS) is on use of remote services and resources existing in a networked computer system. In distributed operating system, the focus is on effective utilisation of resources in distributed computing environment.
1. Unified User Experience
In a Distributed OS, multiple computers work together to appear as a single system to the user. This means:
The user doesn't need to know where files or processes are physically located.
They can access resources seamlessly, as if all data and programs are on one system.
Why better?
Because users don’t have to log into separate machines or remember different resource locations — saving time and reducing complexity.
2. Automatic Resource Management
A Distributed OS automatically manages:
Resource allocation (CPU, memory, files)
Task scheduling
Load balancing
It distributes work based on system load, availability, and efficiency.
Why better?
In a Network OS, these decisions must be made manually by the user or administrator, which can lead to inefficiencies or underutilized systems.
4.(b) Write the step-by-step procedure to create a group named "MCS22". Now add a user "Kamal" in Windows 2000 operating system. Assume user "Kamal" is already a member of the guest account in your system.
Sol: Procedure to Create Group "MCS22" and Add User "Kamal" in Windows 2000
Step 1: Open "Computer Management"
Right-click on My Computer on the desktop.
Click on Manage.
This opens the Computer Management window.
Step 2: Navigate to Local Users and Groups
In the left pane, expand the option:
System Tools → Local Users and Groups
You will see Users and Groups listed.
Step 3: Create a New Group "MCS22"
Click on Groups.
In the right pane, right-click and select New Group.
In the Group Name field, type: MCS22
Optionally, add a description.
Click Create, then click Close.
Step 4: Add User "Kamal" to Group "MCS22"
In the Groups list, double-click on MCS22.
In the Group Properties window, click on Add.
In the "Enter the object names to select" field, type: KAMAL
Click OK.
Click Apply, then OK to close.
Step 5: Verify the User Addition (Optional)
Still in Computer Management, click on Users.
Double-click the user Kamal.
Go to the Member Of tab.
You should now see both:
Guests
MCS22
Final Note
Now, the user Kamal is a member of both:
The default Guest group
The new custom group MCS22
4 (c) What is X-Window system ? Explain the X-Window library and X-Toolkit.
Sol: X Window system is supported by an X Consortium of primarily UNIX-based hardware and software vendors as a standard base for user interfaces across most UNIX product lines. The X Window system does not define any particular style of interface but rather provides a mechanism for supporting many styles. X is also network-based.
The X architecture is based on the premise that an application can run one computer, while the graphical presentation of the application's output and responses from the user can occur on another computer. As such, X provides a flexible set of primitive window operations but carefully avoids dictating the look and feel of any particular application. X does not provide user interface components such as buttons, menus, or dialog boxes.
X-Window Library: One standard programming interface to X is the C language library known as X Library or Xlib. This library defines functions for access and control over the display, windows and input devices.
X-Toolkit: X Toolkit is the foundation upon which most of the commercial toolkits are based and is a good example for describing object-oriented functionally. The X Toolkit consists of two parts: a layer known as Xt Intrinsics and a set of widgets. The widget set implemellts user interface components including scroll bars, menus and buttons. Xt intrinsics provides a framework that allows the programmer to combine the components. Both parts are integrated with Xlib, allowing programmers access to higher-level libraries.
A typical X programming environment is illustrated in Figure:
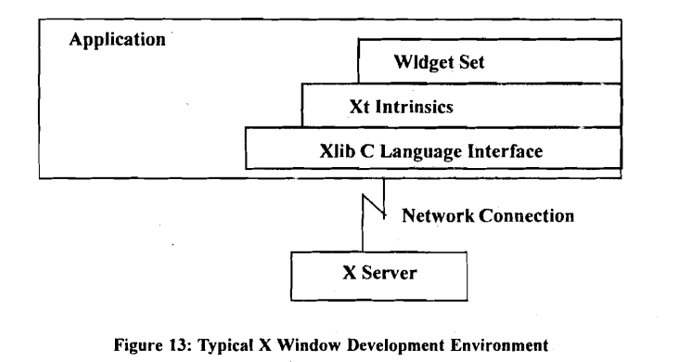
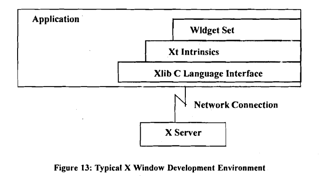
The X application programmer is likely to use a combination of a higherlevel toolkit (e.g., theToolkit's Xt Intrinsic), Xlib, and a widget set. The class library programmer, whose job is to create new widgets, is likely to use the capabilities from within one of the higher-level toolkits.
4.(d) Explain the characteristics of multiprocessor operating system.
Sol: A typical multiprocessor system consists of a set of processors that share a set of physical memory blocks over an interconnection network. Thus, a multiprocessor system is a tightly coupled system where processors share an address space. A multiprocessor operating system controls and manages the hardware and software resources such that users view the entire systems as a powerful uniprocessor system; a user is not aware of the presence of multiple processors and the interconnection network.
Characteristics
There are multiple processors.
These processors share the same main memory and I10 facilities, interconnected by a communications bus or other internal connection scheme.
All processors can perform the same functions (hence the term Symmetric).
Pesformancc: If the work to be done by a computer can be organised so that some portions of the work can be done in parallel, then a sysfe.-., with multiple processors will yield greater performance than one with a single processor of the Introduction to same type.
Faster Processing
Execution of programs becomes faster because different parts of a program or different processes can run in parallel.
Shared Memory Architecture
All processors share the main memory.
This makes communication between processors faster and more efficient compared to distributed systems.
5. Write short notes on the following :
(a) LAN Topologies
(b) Optical Fibers
(c) Network Monitoring Tools
(d) Active Directory in Windows 2000
(a) Lan Topologies: Most commonly used LAN topologies are Bus, Ring, Star and Mesh Topologies.
Bus Topology : In the bus topology there is a single bus that carries all the data to the entire network. A bus is a single continuous communication cable to which all the computers are connected. A cable or bus runs throughout tlie office to which all the workstations are connected. The bus topology is also known as linear bus.
When one workstation wants to talk to another the message or signal travels down the bus in both directions. Each one reads the message to see if it matches its address. The bus topology is a passive topology. It means that the computers connected to the bus amplify the signal on the bus.
A network with bus topology cannot become too big as all the traffic is on a single bu;. The entire network can be down only if the bus has a break.
Ring Topology: In the ring topology all the workstations are connected in the shape of a ring. The ring does not have an end. It is made up of short segments that' connect one PC to the next and so on, until all the computers are joined in a circle. The signals travel only in one direction and from one PC to tlie next until it reaches the appropriate node. It is also difficult to move a workstation or to add more computers to an existing ring.
The ring topology is an active topology. Each computer boosts the signal (like a repeater) and passes to the next computer till it reaches the destination computer. A drawback of this topology is that if one computer fails, tlie entire network is down.
Star topology: In tlie star topology all the stations are connected to a central computer or hub creating a star configuration. The devices are not directly linked to each other Messages pass from the nodes to the hub, where they are processed or passed along to another node. The hub controls the traffic on tlie network. If the hub fails, the entire network becomcs inoperative, but if a node fails it does not affect the rest of the traffic on the network.
Mesh Topology: In a mesh topology, every node has a dedicated point-to point link to every other node. Simply dedicated means that the links carry traffic only between the two nodes. So mesh topology does not have traffic congestion proble~ns every node has n-1 link,for a fully connected mesh topology Iiaviug n nodes.
(b) Optical Fibers: Optical fiber consists of thin glass fibers that can carry information at frequeit-ies in the visible light spectrum and beyond. The typical optical fiber consists of a very narrow strand of glass called the core. Around the core a concentric layer of glass called the cladding. Coating the cladding is a protective coating consisting of plastic, it is called the Jacket.
Optical fibers work on the principle that the core refracts the light and the cladding. reflects the light.
Advantages of Optical Fiber
Noise immunity: RFI and EM1 immune (RFI - Radio Frequency Interference, EM1 -Electromagnetic Interference) because fiber -optic transmission uses light rather than electricity, noise is not a factor.
Security: cannot tap into cable
Large Capacity due to BW (bandwidth).
No corrosion.
Longer distances than copper wire.
Smaller and lighter than copper wire.
Faster transmission rate.
Disadvantages of optical fiber
Physical vibration will show up as signal noise.
Limited physical arc of 'cable. Bend it too much and it will break.
Difficult to splice.
(c) Network Monitoring Tools: Network monitoring tools are software applications that track, analyze, and report on the performance of a network, including hardware, interfaces, storage devices, and virtual environments.
1. Wireshark
Open-source packet analyzer.
Captures and inspects data packets in real-time.
Helps in troubleshooting network issues and analyzing protocols.
2. Nagios
Monitors network services like HTTP, FTP, SMTP, etc.
Sends alerts when systems go down and when they recover.
Supports plugins for customization.
3. PRTG Network Monitor
All-in-one monitoring for bandwidth, usage, and devices.
Offers customizable dashboards.
Suitable for small to large-scale networks.
